Re: Collecting entropy from device_attach() times.
On Thursday, September 20, 2012 6:21:04 am Pawel Jakub Dawidek wrote:
> On Wed, Sep 19, 2012 at 11:10:51PM +0100, RW wrote:
> > On Wed, 19 Sep 2012 22:53:32 +0200
> > Pawel Jakub Dawidek wrote:
> >
> >
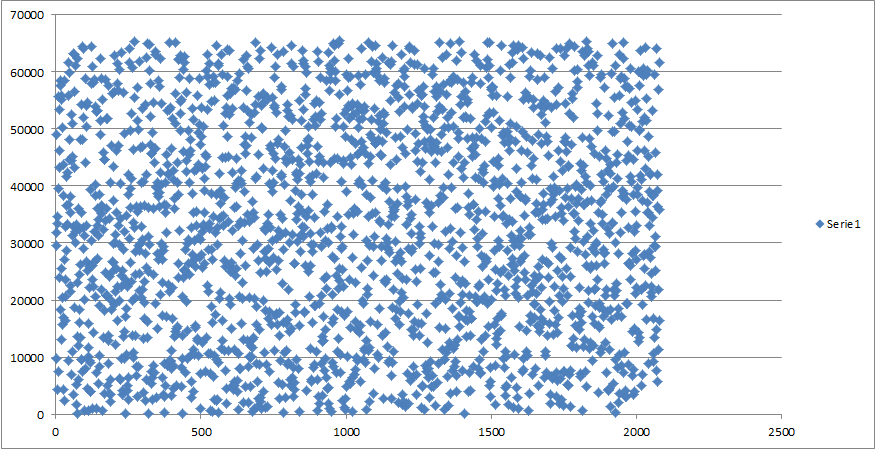
> > > Here's how the distribution looks like for device_attach() times of my
> > > sound card. The times were 26bit numbers, so this is after discarding
> > > top ten bits, which leave us with 16 lower bits of pure entropy:)
> > >
> > > http://people.freebsd.org/~pjd/misc/harvest_device_attach.png
> >
> >
> > You're basing a model for all devices on a single sound card, that
> > doesn't seem safe to me. Isn't it possible that a device could take a
> > long and well defined time? Some interrupts can carry a lot of entropy
> > but they are still only accounted at 2 bits.
>
> I agree, we should do such analysis for much more devices and different
> kind of devices. A platform might be an important factor as well.
> It is hard to collect decent number of probes when reboot is needed, so
> what I'd recommend is to turn of SMP, boot into single module and
> kldload/kldunload a driver in a loop, of course with kernel patched to
> log those times.
This is not always representative. Any driver that uses a config intrhook
will run that synchronously during attach() in single user mode but will
not during boot. config intrhook's often go out and do things that take a
variable amount of time (poking hardware, waiting for interrupts, etc.).
That means that timing any such drivers from single user mode will likely
give you more variable attach() times than would occur during boot.
--
John Baldwin
_______________________________________________
freebsd-security@freebsd.org mailing list
http://lists.freebsd.org/mailman/listinfo/freebsd-security
To unsubscribe, send any mail to "freebsd-security-unsubscribe@freebsd.org"
討論串 (同標題文章)
完整討論串 (本文為第 30 之 80 篇):